Posted: April 6th, 2017 | Author: jordan | Filed under: Linux, Work | No Comments »
 Recently I was lucky enough to be a crew member on a sailboat that was making passage through the Caribbean. The Captain of the vessel, who lived aboard, was speaking to me about data storage and how difficult of an equation it was. Sailboats have very little power available to them when they’re underway as most don’t run their engine which is the only source to power the limited batteries kept onboard. He was thinking about picking up a Drobo-Mini and using SSDs to reduce the amount of draw on his system, however this solution is DAS based and doesn’t allow him access to the data unless he plugs directly into the box which means, you need a computer as well. Which is even more draw on the electrical system.
Recently I was lucky enough to be a crew member on a sailboat that was making passage through the Caribbean. The Captain of the vessel, who lived aboard, was speaking to me about data storage and how difficult of an equation it was. Sailboats have very little power available to them when they’re underway as most don’t run their engine which is the only source to power the limited batteries kept onboard. He was thinking about picking up a Drobo-Mini and using SSDs to reduce the amount of draw on his system, however this solution is DAS based and doesn’t allow him access to the data unless he plugs directly into the box which means, you need a computer as well. Which is even more draw on the electrical system.
After a quick think and a look around the Internet I decided that the best way to address this issue would be to use a Raspberry Pi 3, a four port USB hub, Â multi-SD card reader, and mdadm, with smb, nfs, and upnp. I’m not going to go into the nitty gritty of how to setup a raspberry pi as there are many tutorials available online already. However I will touch on some performance metrics that I was able to pull.
It’ll be small physically, have very little power draw, each microSD card draws between 66–330 mW during data transfer, at idle 0.2mA. Each bank will be less than 1mA at idle and 1.2W during transfer. Each bank should yield close to 800GB, all together I’ve calculated 3.2TB of data storage at 6-8W. Pretty dope hey?
The issue is cost. Prices in CAD
Computation
Raspberry Pi is $60
case and parts $20
USB Hub $26
total: $106 plus tax / shipping
Data Storage
Four card reader $20
200GB microSD card $91
800GB bank total $384 plus tax / shipping
Performance
Performance will max out at around 40MB/sec which isn’t great however we’re not looking for performance we’re looking for efficiency.
I welcome comments to this plan below

My next step to this plan would be to get the Pi to be a wireless access point as well.
Posted: February 27th, 2013 | Author: jordan | Filed under: Blog, DNS, Kerberos, krb5, LDAP, Linux, Networking, Work, Zentyal | 4 Comments »
Get a terminal session on your Zentyal box and install the VNC service
sudo apt-get install vnc4server
Next, run the server once to initialize a config file, kill the service and make a backup of the config file and then edit.
vncserver
vncserver -kill :1
cp .vnc/xstartup .vnc/xstartup.bak
nano .vnc/xstartup
Uncomment one line and add another:
# Uncomment the following two lines for normal desktop:
unset SESSION_MANAGER
# exec /etc/X11/xinit/xinitrc
/usr/bin/lxsession -s LXDE -e LXDE
Then just launch
vncserver
Watch the output so you can ensure what port to connect to. For example, the following means my VNC server is listening on port 5901
jordan@mrsparkle:/etc/X11$ vncserver
New 'mrsparkle:1 (jordan)' desktop is mrsparkle:1
Starting applications specified in /home/jordan/.vnc/xstartup
Log file is /home/jordan/.vnc/mrsparkle:1.log
Posted: September 8th, 2011 | Author: jordan | Filed under: Blog, CentOS, Linux, Networking, Xen | No Comments »
Overview
In this how-to we’re going to install CentOS 5.5 and prep it to become a virtual machine server. Before proceeding PLEASE read our Xen software page so you understand how the VM and network topology works. This how-to was built combining various methods publicly already available. If you find some copy and pasted text just remember: a good sysadmin is a lazy sysadmin.
Prerequisites
LACP bonded 802.1q trunk with necessary VLAN’s assigned
Installation
Install CentOS 5.5, during the package selection screen make sure to enable the Virtualization option.
Configuration
First let’s make sure that xen is running properly. Log into the GUI of the server, if you do not have a GUI then log into an ssh session as root with X forwarding on. Run virt-manager from the console. You should see “dom0” running, if you double click on it you’ll be able to see the statistics for this domain and how much resources it is consuming. If you cannot see this or if virt-manager does not find a dom0 to connect to you have done something wrong. I cannot help you.
1. Physical Networking Devices
What we first need to do is setup our networking devices.
Edit some files in /etc/sysconfig/network-scripts. Remember that bond0 is the physical interface that the trunk is connected to therefore it does not need an IP address.
# ifcfg-bond0
DEVICE=bond0
BOOTPROTO=none
ONBOOT=yes
USERCTL=no
TYPE=BOND
BONDING_OPTS="mode=4"
#ifcfg-eth0
DEVICE=eth0
BOOTPROTO=none
ONBOOT=yes
MASTER=bond0
SLAVE=yes
USERCTL=no
TYPE=Ethernet
HWADDR:(MAC-ADDRESS OF ETH0)
#ifcfg-eth1
DEVICE=eth1
BOOTPROTO=none
ONBOOT=yes
MASTER=bond0
SLAVE=yes
USERCTL=no
TYPE=Ethernet
HWADDR:(MAC-ADDRESS OF ETH1F)
Then for every VLAN that you are passing in your trunk create a file as follows. Please replace the ‘N’ with the VLAN ID number
[root@xentest jeunson]# more /etc/sysconfig/network-scripts/ifcfg-bond0.N
DEVICE=bond0.N
BOOTPROTO=none
#IPADDR=192.168.100.51
#NETMASK=255.255.255.0
ONBOOT=yes
VLAN=yes
TYPE=BOND
Note how the IP address is commented out on this VLAN interface. You can assign an IP address to the VLAN interface that will be the management interface for the hardware.
Finally don’t forget to add the following line to /etc/modprobe.conf
alias bond0 bonding
Now that you’ve created the VLANs and assigned a management interface we edit the file /etc/sysconfig/network
[root@xentest jeunson]# more /etc/sysconfig/network
NETWORKING=yes
NETWORKING_IPV6=no
HOSTNAME=xentest.example.com
GATEWAY=192.168.101.254
GATEWAYDEV=bond0.101
Now restart the networking with /etc/init.d/network restart It should restart with out any errors
Shutting down interface bond0.100: Removed VLAN -:bond0.100:-
[ OK ]
Shutting down interface bond0.101: Removed VLAN -:bond.101:-
[ OK ]
Shutting down interface bond: [ OK ]
Shutting down loopback interface: [ OK ]
Disabling IPv4 packet forwarding: net.ipv4.ip_forward = 0 [ OK ]
Bringing up loopback interface: [ OK ]
Bringing up interface bond0.100: Added VLAN with VID == 100 to IF -:bond0:-
[ OK ]
Bringing up interface bond0.101: Added VLAN with VID == 101 to IF -:bond0:-
[ OK ]
 2. Xen Networking Scripts
2. Xen Networking Scripts
First modify /etc/xen/xend-config.asp and change the netdev device from eth0 to bond0. You’ll probably have to reboot the computer.
A.Modify the network-bridge script
Now that we’re done that we need to configure Xen to tell it what networking interfaces to use. First make a backup of the xen network-bridge script and edit as follows.
cp /etc/xen/scripts/network-bridge /etc/xen/scripts/network-bridge.orig
Change around line 78 from
[ -f "/sys/class/net/$1/bonding/slaves" ]
to
[ -f "/sys/class/net/$1/bonding/slaves" ] || [ -f /proc/net/vlan/$1 ]
B. Modfiy xend-config.sxp
The second change involves modifying the xend configuration file to use a new network initialization script.
[root@xentest scripts]# cd /etc/xen
[root@xentest scripts]# cp -p xend-config.sxp xend-config.sxp-dist
Change the network-script configuration directive to the new script name – such as network-multi-bridge. After the modification:
[root@xentest xen]# diff xend-config.sxp-dist xend-config.sxp
91c91
< (network-script network-bridge) --- > (network-script network-multi-bridge)
C. Create network-multi-bridge script
This script uses the two VLAN interfaces previously defined.
[root@xentest scripts]# cd /etc/xen/scripts
[root@xentest scripts]# more network-multi-bridge
#!/bin/sh
dir=$(dirname "$0")
"$dir/network-bridge" "$@" vifnum=0 netdev=bond0 bridge="xbr_trunk"
/sbin/ifup eth0.100
“$dir/network-bridge” “$@” vifnum=1 bridge=”xbr_v100″ netdev=”bond0.100″
/sbin/ifup eth0.101
“$dir/network-bridge” “$@” vifnum=2 bridge=”xbr_v101″ netdev=”bond0.101″
At this point you should reboot your server to make sure that everything comes up cleanly. Use the logs to debug problems and look out for which type of bond your computer connects to the switch as.
Posted: March 20th, 2011 | Author: jordan | Filed under: LDAP, Linux | Tags: apache, authentication, Directory, ldap, ldap-group, open ldap | 2 Comments »
OK peoples, this one frustrated me for a bit, but because I’m stubborn I figured it out.
I have a webservice that I want to protect by using LDAP authentication within Apache from our OpenLDAP server. However, you want to make sure that the user belongs to a specific LDAP group. If you’re like me your groups look something like this:
bart:~ jordan$ ldapsearch -h ldap.shop.lan -x -b "dc=shop,dc=lan" cn=fgstaff
# extended LDIF
#
# LDAPv3
# base with scope subtree
# filter: cn=fgstaff
# requesting: ALL
#
# fgstaff, Groups, shop.lan
dn: cn=fgstaff,ou=Groups,dc=shop,dc=lan
cn: fgstaff
gidNumber: 1022
description: Staff
objectClass: posixGroup
memberUid: jordan
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
So to make it work you need a few things inside of your Directory tag for the virtual host config file. First, here’s mine:
Options FollowSymLinks
AllowOverride None
AuthName "FG Staff ONLY!"
AuthType Basic
AuthBasicProvider ldap
AuthzLDAPAuthoritative on
AuthLDAPURL "ldap://1.1.1.1/ou=People,dc=shop,dc=lan?uid"
require ldap-group cn=fgstaff,ou=Groups,dc=shop,dc=lan
AuthLDAPGroupAttributeIsDN off
AuthLDAPGroupAttribute memberUid
The trick for me was putting in the require ldap-group plus the whole path including container, org unit, and the dc’s. Then AuthLDAPGroupAttributeIsDN. This is big because if it is on then apache will check if “memberUid=uid=jordan ou=People” is part of the fgstaff group and not just “jordan”
Once I set this, it all worked. I’m hoping this will help any others out there.
Posted: February 22nd, 2011 | Author: jordan | Filed under: Linux | Tags: ubuntu server, vtiger | No Comments »
 I tried to install vTiger from the .bin file on their website. I tried CentOS, Ubuntu, and OpenSuSE. None could get through the installer without crashing. So I said forget it and installed from source. I spent over 3 hours with different distros trying to get the .bin file to work. It took me 15mins to figure it out from source.
I tried to install vTiger from the .bin file on their website. I tried CentOS, Ubuntu, and OpenSuSE. None could get through the installer without crashing. So I said forget it and installed from source. I spent over 3 hours with different distros trying to get the .bin file to work. It took me 15mins to figure it out from source.
Here are step by step instructions on how to install vTiger 5.2.1 on a virgin Ubuntu Server 10.04 LTS Server:
Download vTiger 5.2.1 source and extract tarball to /srv/www
use apt-get to install the following packages:
apt-get install mysql-server apache2-utils libapache2-mod-php5 libgd-tools php5-gd php5-imap php5-mysql
Then chown the /srv/www directory to the apache user.
chown -R www-data /srv/www
Create a vhost file for the service. Copy this into /etc/apache2/sites-available/vtiger.
Then link this file into the sites-enabled directory
ln -s /etc/apache2/sites-available/vtiger /etc/apache2/sites-enabled/030-vtiger.conf
Ensure your apache and mysql services are running.
service apache2 restart
service mysql restart
Open up a web browser and navigate to your server’s IP address. You should be greeted with a prompt to install the wizard, this wizard will help you plugin your details as well as help you edit your /etc/php5/apache2/php.ini file. For the mysql address specify you loopback 127.0.0.1.
After that you should be good to go!
Posted: May 31st, 2010 | Author: jordan | Filed under: Insight, Linux | No Comments »

The Folks
Someone the other day asked me about how I got into the computer industry, and I guess it was because of my father. I still remember the day he brought home our first Commodore 64. The excitement I felt as the disk drive began to makes noises that are reminiscent to some sort of steam punk robot still resonates within me today. I was roughly eight but from that day on I was hooked, especially when I figured how to use a modem. If my parents read my blog they’re about to read a story regarding a strange incident from the past.
We had a 300 Baud modem that my father thought didn’t work and tossed aside, it came with a program called Quantum Link which eventually turned into AOL. I figured out how this modem worked by reading our subscription to the Computing Monthly Magazine and eventually got connected to a BBS in Toronto. Toronto, the city.
Now if you’ve been around long enough you’ll remember that most BBS were crowded services that were hard to get onto as they were all modem based, and if run out of house only had one line dedicated to it. In addition, since modem operate on phone lines you had to physically call the other end, so if the BBS was in Toronto you were basically making a long distance phone call.
My parents could NOT figure out what this number was that racked up so much long distance, and why it would just squeal when they called it. They called the phone company and I think got the charges reversed but I didn’t want this to happen again. I told some friends of mine who also had a Commodore 64 and they showed me that if you use a touch tone telephone to navigate through an automated phone system at BC Gas you could get to an open relay and make free long distance calls.
Through the years I’ve learned more and more and eventually got to the point where it’s now my profession. With this comes the need to have servers and there’s just something gratifying in having that “server under the bed.” My parents just so happen to have a spare bedroom in their house and thus the perfect place for my server to live. However every so often it needs some maintenance and thus my Dad is the one who intervenes. Recently though the requests I’ve been making of him have been getting more and more complicated and so I wrote a Linux Command Shell 101, to which I now share with you world. For all you people learning the shell for the first time.
Hi Dad,
So I’ve decided that it’s time you learn the command shell in Linux and how to use it. Yes, you have to read this 
Chapter 1 – The Shell
The shell is actually not that complicated, but if you don’t understand what you’re looking at it can be very confusing. First what is a command shell? Well it’s actually no different than a programming language. It’s a way of giving the computer commands and interacting with it in either one off commands or in a script. There are many types of shells as well, the most common is the Bourne Again SHell or BASH for short, for the most part this is the defacto standard shell. Some other shells are:
ash
kash
tsh
tcsh
Most shells are all the same thing, the only difference between them is small grammatical differences. For example, and don’t worry that you have no idea what this is about.
bash ${variable}
ash $variable
kash $|variable|
see? small differences. So in summary the shell is a place where you can input commands to the computer and the computer executes them for you.
Next is a look at the shell. The following is what my shell looks like on my mac.
bart:~ jordan$
This is a command prompt. When you see something like this it means that computer is ready to accept commands.
So there are a few pieces of information here.
The first word tells us the name of the computer. In this case, my computer’s name is bart. Another word for the computers name is hostname
“:” indicates the end of the hostname,
“~” tells us the path that we are currently located (more about path later)
then username that we’re currently logged in as.
The $ tells us its the end of the prompt.
Now some prompts may look a little different from this but they’ll be the same more or less. Here’s what it looks like when I’m logged in as root
bart:~ root#
notice the only difference is the end of the prompt has a pound symbol instead of a dollar sign. This is because we’re root. All users prompts end in a dollar sign but only the root user ends in a pound. So if you ever encounter a prompt with nothing but just a dollar sign OR a pound you’ll still know that its a prompt.
Chapter 2 – Command Structure
Now it’s time to give the computer a command. You already know what a command is, its basically a program that runs in text mode. Commands can be anything from something simple like “cd” (change directory) to something complicated like “firefox-text” (text mode on firefox) When you give a shell a command there are a few things that you need to be aware of. First is a switch.
Switchs
A switch is a modifier that you give to the command to change what the command does. For example the command “ls” gives a listing of the files in the current directory. So here’s an example of the ls command listing the files in my home directory.
bart:~ jordan$ ls
Applications Downloads Movies Public bin
Desktop Library Music Sites test
Documents LimeWire Pictures bash.test zimbra
bart:~ jordan$
Now what I’m going to do is give the same command but with the -l switch. (that’s a lower case L)
bart:~ jordan$ ls -l
total 16
drwxr-xr-x 3 jordan staff 102 12 May 23:40 Applications
drwx------ 20 jordan staff 680 22 May 02:41 Desktop
drwxr--r--@ 39 jordan staff 1326 12 May 23:31 Documents
drwx------ 40 jordan staff 1360 18 May 09:22 Downloads
drwx------ 47 jordan staff 1598 23 May 20:01 Library
drwxr-xr-x 4 jordan staff 136 12 Feb 10:09 LimeWire
drwx------ 12 jordan staff 408 16 May 23:17 Movies
drwxr--r-- 21 jordan staff 714 24 Mar 19:41 Music
drwxr--r-- 23 jordan staff 782 7 May 23:33 Pictures
drwxr-xr-x 5 jordan staff 170 16 Sep 2009 Public
drwxr-xr-x@ 7 jordan staff 238 2 Nov 2009 Sites
-rwxr-xr-x 1 jordan staff 73 23 May 15:03 bash.test
drwxr-xr-x 6 jordan staff 204 7 May 23:33 bin
-rw-r--r-- 1 jordan staff 19 18 May 12:07 test
drwxr-xr-x 3 jordan staff 102 9 May 17:40 zimbra
bart:~ jordan$
see how command changes? It’s the same command, it does the same thing in that it lists all the files and folders but it also gives me LOTS of other options such as owner, size, date, etc.
Arguments
Next is an argument, an argument usually goes with a switch. So say you have a command like a text editor. One example of a text editor is “nano” if you just type edit the computer will not do anything, you have to give it a file to edit as well. So for example:
nano example.txt
We see here that “nano” (which is used as an example only) is the command and “example.txt” is the argument.
Final Chapter – Commands
Finally I’m just going to touch a few basic and extremely common commands as well as a way of searching for commands and their manuals. First let’s introduce you to a utility called “apropos” To use apropos you simply type it in followed by an argument in quotations. ie: apropos “move files” What this will do is search all the commands available on your computer for something that matches “move files” Think of it as a search engine for commands, a really dumb search engine. It’s dumb because if you don’t pick the right words to search for it won’t find anything. Take this for example. apropos “make folder” will find nothing but apropos “create folder” will have many search results.
So let’s use apropos to find a command to move files
bart:~ jordan$ apropos "move files"
mv(1) - move files
removefile(3), removefile_state_alloc(3), removefile_state_free(3), removefile_state_get(3), removefile_state_set(3) - remove files or directories
srm(1) - securely remove files or directories
bart:~ jordan$
So in the search results here there are the actual commands on the left (ignore the number in the brackets) and then explanations on the right. The first line looks like the one the that we want, the second (and third) line looks like garbage and the last line is some command to remove files. Apropos found the last line because we searched for move files and reMOVE FILES matches that. See how it’s dumb?
Ok so the command we want is the first line, mv. Next we need to learn how to use this command, what switches and arguments it can take so what we do is use another command called “man” man is short for manual. Simple. We type man and then the command name as an argument. for example
bart:~ jordan$ man mv
MV(1) BSD General Commands Manual MV(1)
NAME
mv -- move files
SYNOPSIS
mv [-f | -i | -n] [-v] source target
mv [-f | -i | -n] [-v] source ... directory
DESCRIPTION
In its first form, the mv utility renames the file named by the source
operand to the destination path named by the target operand. This form
is assumed when the last operand does not name an already existing direc-
tory.
In its second form, mv moves each file named by a source op...... ETC ETC ETC
To navigate this man page you can use the up and down arrows as well as the page up and page down keys. To exit push “q”
There you have it between apropos and man you can search and learn all commands linux. Here are a few commands that very important for you to know.
ls: list files and folders in current directory
cd: change directory
mkdir: make directory
rm: remove file
rm -rf: remove files and folders, WITHOUT VERFICATION
mv: move files and folders
pwd: display current directory
whoami: display your username
nano: an easy to use text editor, to use it just type “nano ”
exit: exits the shell
Ok, so this is pretty short and brief but hopefully was a good introduction to the Linux command shell. If you have questions or if something I wrote doesn’t make sense email me back and let me know.
Posted: May 24th, 2010 | Author: jordan | Filed under: Kerberos, krb5, LDAP, Linux, Mac OS X Server, Snow Leopard | 1 Comment »
This is an extension article to my previous article Open Directory, Kerberos, Single Sign On (SSO) and CentOS with SSH and Kerberized NFS Home Directories. I had some requests from different Linux users out there how to incorporate authentication for Linux flavours other than CentOS. For this example we’re going to use Debian Lenny with some Ubuntu 10.04 refs thrown in.
Preperation – LDAP
First download all the packages that we’ll need.
Debian
apt-get install nss_updatedb ldap-utils libpam-ldap libnss-ldap nscd
Ubuntu
apt-get install nss_updatedb ldap-utils libpam-ldap libnss-ldap nscd nslcd
During the installation debconf should ask you some questions, here are my answers
LDAP server Uniform Resource Identifier: ldap:/// (Note the "ldap://", NOT "ldapi://"!)
Distinguished name of the search base: dc=foo,dc=bar
LDAP version to use: 3
Does the LDAP database require login? No
Special LDAP privileges for root? No
Make the configuration file readable/writeable by its owner only? No
Make local root Database admin. No
Does the LDAP database require login? No
Local crypt to use when changing passwords. crypt
If you’re not on Debian you can edit these options in the file /etc/ldap/ldap.conf and /etc/libnss-ldap.conf
Next, edit /etc/nsswitch.conf and change
passwd: compat
groups: compat
--to--
passwd: files ldap
groups: files ldap
Now restart the nscd service ( and nslcd if you’re using Ubuntu 10.04 )
Verify you can see the users via LDAP with the id or getent commands
jordan@elm:/$ id jordan
uid=1000(jordan) gid=100(users) groups=1001(ldap-admin),1022(fgstaff),1023(ssh-access),100(users)
jordan@elm:/$ getent passwd | grep jordan
jordan:x:1000:100:Jordan Eunson:/net/home/jordan:/bin/bash
jordan@elm:/$
Preperation – libpam-krb5
Download and install the packages
apt-get install krb5-config libpam-krb5
Then edit your /etc/krb5.conf file. Now here what you *could* do is copy the one from you Mac. If you have a Mac client already bound to your Open Directory installation then open the file /Library/Preferences/edu.mit.Kerberos and copy and paste the content to /etc/krb5.conf
Here is an example of mine for the realm FOO.BAR
[libdefaults]
default_realm = FOO.BAR
[realms]
FOO.BAR = {
admin_server = od-master.foo.bar
kdc = od-master.foo.bar
}
[domain_realm]
.foo.bar = FOO.BAR
foo.bar = FOO.BAR
[logging]
admin_server = FILE:/var/log/krb5kdc/kadmin.log
kdc = FILE:/var/log/krb5kdc/kdc.log
To test to see if this is working type the command kinit and see if we can get a ticket from the Kerberos Key Distribution Center
bart:~ jordan$ kinit jeunson
Please enter the password for jeunson@FOO.BAR:
bart:~ jordan$ klist
Kerberos 5 ticket cache: 'API:Initial default ccache'
Default principal: jeunson@FOO.BAR
Valid Starting Expires Service Principal
05/24/10 16:30:35 05/25/10 02:29:14 krbtgt/FOO.BAR@FOO.BAR
renew until 05/31/10 16:30:35
bart:~ jordan$
Kerberos Authentication
Now that we have our Kerberos client working we can integrate the local system to LDAP for user lookup and Kerberos for passwords with PAM libraries.
/etc/pam.d/common-account
account sufficient pam_unix.so
account required pam_krb5.so
/etc/pam.d/common-auth
auth sufficient pam_unix.so nullok_secure
auth sufficient pam_krb5.so use_first_pass
auth required pam_deny.so
/etc/pam.d/common-session
session required pam_unix.so
#session required pam_mkhomedir.so skel=/etc/skel/ umask=0022
session optional pam_krb5.so minimum_uid=1000
Now try to login to your Linux client either on the console to see if it works. To finish up with Kerberizing the client please read this article
Posted: May 17th, 2010 | Author: jordan | Filed under: Kerberos, krb5, Linux, Mac OS X Server, Snow Leopard, SSH | 1 Comment »
This article is a pseudo continuation of the article: Using Network Accounts on a Linux Client with Open Directory Leopard Server. In this article I’m going to be going over at a high level the single sign-on environment in Mac OS X Server and at a low level on integrating Kerberized SSH and NFS and CentOS.
Please note the benefits of Kerberized NFS is that if a local computer is compromised the attacker will not be able to read NFS shares because they will not have a valid Kerberos ticket. Oh… and the whole NFS stream will be encrypted. (pow!)
Open Directory and Kerberos
 Taken from Apple’s site: Picture walking into the local county fair, and you are given two choices. You can either use your credit card at the entry of every ride or you can use it once at a booth, which grants you a ticket that you can use for the remainder of the day. It’s a pretty simple choice if you’re concerned about the security of your credit card information and want to have a hassle-free day at the park.
Taken from Apple’s site: Picture walking into the local county fair, and you are given two choices. You can either use your credit card at the entry of every ride or you can use it once at a booth, which grants you a ticket that you can use for the remainder of the day. It’s a pretty simple choice if you’re concerned about the security of your credit card information and want to have a hassle-free day at the park.
This is exactly what Kerberos accomplishes in its implementation of Single Sign On in network environments. At the beginning of the workday, a user enters his/her password into the system once; this action decrypts a ticket from a server running as a Kerberos Key Distribution Center (KDC). The ticket holds a set of encrypted keys, which are used throughout the day to authenticate user access without exchanging sensitive password information. It expires after a given amount of time (typically one day), so even if a would-be intruder sniffs it out and decrypts the information, the user-access information remains safe in the long term.
With your Kerberos ticket you can be granted password-less access to services across a multitude of platforms. You could be on your Mac client with a valid Kerberos ticket and authenticate to a Linux VNC server, or a Mac AFP/NFS server, or a simple SSH session. The possibilities are mind blowing!
As a side note: in this article the OD master will be referred to as foo and the linux client named lame with the domain of example.bar
Open Directory and Kerberos Setup
This article assumes your are somewhat of a valid Systems Admin and were able of getting your OD environment up and running without issue. If not please read: http://www.makemacwork.com/master-open-directory-1.htm
At a real high level here are the steps:
- set the hostname of your OD master
- in Server Admin turn DNS on and setup
- use `dig` to verify your forward and reverse DNS records to your OD master
- set Open Directory in Server Admin to `Open Directory Master`
- start binding clients
Extra tip and trick. In Server Admin -> Open Directory, there is an option I believe under Policy->binding that says something to effect of: Require authenticated binding between Directory and Clients. Enable this, then bind your Mac clients. What it will do when binding is ask for a username and password and computer record, enter your diradmin credentials and the FQDN of the host you are binding. For example, if your domain is example.bar and your client’s hostname is foo then enter: foo.example.bar
Kerberized SSH
For the Mac use /Applications/Utilities/Directory Utility to bind your Mac to the OD master.
On the Linux / CentOS side we’re going to setup Kerberos. First install kerberos with yum
sudo yum install krb5-auth-dialog krb5-devel krb5-libs pam_krb5-2.2.14-10 krb5-workstation
Now from the Gnome GUI go to System->Administration->Authentication
- Check, Enable LDAP Support
- Enter your LDAP search base and server address. Mine for this example would look like:

- If you don’t know your LDAP search base you can get it from the Overview Pane in Server Admin / Open Directory
- Click OK on this dialog box and then select the Authentication tab
- Check Enable Kerberos Support and click Configure Kerberos
- The realm should be the same as your LDAP search base in a different format, mine looks like this:
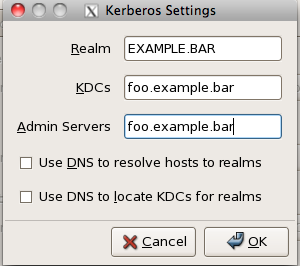
After binding your Mac and Linux clients let’s check to make sure it works. On either client type on the terminal kinit type in your password and then check to make sure you got your Kerberos ticket with klist. You should get the following response.
bart:~ jordan$ kinit jeunson
Please enter the password for jeunson@EXAMPLE.BAR:
bart:~ jordan$
bart:~ jordan$
bart:~ jordan$
bart:~ jordan$ klist
Kerberos 5 ticket cache: 'API:Initial default ccache'
Default principal: jeunson@EXAMPLE.BAR
Valid Starting Expires Service Principal
05/16/10 13:30:30 05/16/10 23:29:36 krbtgt/EXAMPLE.BAR@EXAMPLE.BAR
renew until 05/23/10 13:30:30
The command kinit is what is used to authenticate ourselves to the Kerberos Key Distribution Center (KDC) and grant us access to all Kerberized services. It is essential to have this ticket before proceeding.
Now that we know that Kerberos is working correctly we’re now going to setup Kerberized SSH. For your Mac and Linux clients we’re going to edit /etc/ssh_config or /etc/ssh/ssh_config depending on your Linux distro, you will want the following options set.
GSSAPIAuthentication yes
GSSAPIDelegateCredentials yes
GSSAPIKeyExchange yes
GSSAPITrustDNS yes
For the SSH server on the Mac side set the following options: /etc/sshd_config
GSSAPIAuthentication yes
GSSAPICleanupCredentials yes
GSSAPIStrictAcceptorCheck no
GSSAPIKeyExchange yes
KerberosAuthentication yes
KerberosOrLocalPasswd no
KerberosTicketCleanup yes
For the SSH servers on the Linux side set the following options: /etc/ssh/sshd_config
GSSAPIAuthentication yes
GSSAPICleanupCredentials no
KerberosAuthentication no
KerberosOrLocalPasswd no
KerberosTicketCleanup yes
Restart all SSHd services and make sure you have a fresh ticket from Kerberos.
Testing
First make sure you have a fresh new ticket using kinit and klist. Then try to ssh from your mac client to the Linux server or Mac server. It should let you in automagically. If not run ssh in ultra verbose mode to try and debug the problem. It’s usually comes down to some sort of DNS problem so make sure the Linux server you’re connecting to has DNS records for it and they resolve properly both forwards and reverse.
Kerberized NFS
First, you need to setup an NFS server on your Mac server. I’m not explaining how to do that. But I will say that you NFS mounts should be set to “Any” authentication setting for testing purposes. To learn more read the Apple server manual. 😛
DANGER!
First ensure that the client machine has a DNS record and is resolvable both forwards and reverse and ensure that the /etc/hosts file isn’t treading on the DNS records. Also before we proceed I must make it clear that you are very careful with this section. You will be connecting to the Kerberos Key Distribution Centre that is served inside of your Open Directory server. If you accidentally break something there is a risk that you will break your installation of OD and you will have to rebuild the whole Directory.
SSH in the linux host and check out a kerberos for the directory administrator.
[root@lame]# kdestroy
[root@lame]# kinit diradmin
Password for diradmin@EXAMPLE.BAR:
[root@lame]# klist
Ticket cache: FILE:/tmp/krb5cc_3001_7WM4As
Default principal: diradmin@EXAMPLE.BAR
Valid starting Expires Service principal
05/16/10 23:28:42 05/17/10 09:28:42 krbtgt/EXAMPLE.BAR@EXAMPLE.BAR
renew until 05/17/10 23:27:45
[root@lame]#
With this ticket you can now login to the KDC server. The following command references the file /etc/krb5.conf to locate the KDC server, it is then passed the -p switch with the name of principle to use when connecting.
/usr/kerberos/sbin/kadmin -p diradmin@EXAMPLE.BAR
From here on in, you must be very very careful. This is the Kerberos Key Distribution Centre. We’re going to be adding three principles to the KDC; host, root and nfs. The last one, nfs, requires a special option to make it works. Please make sure to type the FQDN of the linux client.
addprinc -randkey host/lame.example.bar@EXAMPLE.BAR
addprinc -randkey root/lame.example.bar@EXAMPLE.BAR
addprinc -randkey -e des-cbc-crc:normal nfs/lame.example.bar@EXAMPLE.BAR
Now lets copy those principals out of the KDC to the local file system
ktadd -k /etc/krb5.keytab host/lame.example.bar@EXAMPLE.BAR
ktadd -k /etc/krb5.keytab root/lame.example.bar@EXAMPLE.BAR
ktadd -k /etc/krb5.keytab -e des-cbc-crc:normal nfs/lame.example.bar@EXAMPLE.BAR
quit
Make sure this worked by reading the /etc/krb5.keytab file:
[root@lame]# sudo klist -k /etc/krb5.keytab
Password:
Keytab name: FILE:/etc/krb5.keytab
KVNO Principal
---- --------------------------------------------------------------------------
4 host/lame.example.com@EXAMPLE.BAR
4 host/lame.example.com@EXAMPLE.BAR
4 host/lame.example.com@EXAMPLE.BAR
4 root/lame.example.com@EXAMPLE.BAR
4 root/lame.example.com@EXAMPLE.BAR
4 root/lame.example.com@EXAMPLE.BAR
4 nfs/lame.example.com@EXAMPLE.BAR
[root@lame]#
Now there are two daemons that need to be running to make kerberized nfs work. They are rpcgssd and rpcsvcgssd. To get this up we must edit the /etc/sysconfig/nfs file and uncomment the following lines:
MOUNTD_NFS_V3="yes"
SECURE_NFS="yes"
Then start up /etc/init.d/{rpcgssd,rpcsvcgssd} restart
Make sure to add them to the default run level
[root@lame]# /sbin/chkconfig rpcgssd on
[root@lame]# /sbin/chkconfig rpcsvcgssd on
Testing
Let’s try mounting a Kerberized NFS mount. First let’s make the folder /mnt/nfs Now issue a mount command.
sudo mount -t nfs -o sec=krb5p foo.example.bar:/Volumes/Data/Users /mnt/nfs
This "should" mount the NFS share on /mnt/nfs. Use the mount command again to see the krb5p option in action!
Some lines omitted
foo.example.bar:/Volumes/Data/Users on /Volumes/Data/Users type nfs (rw,nosuid,nodev,hard,intr,sec=krb5p,addr=10.10.10.10)
Tada! It Works! 😀
Posted: May 8th, 2010 | Author: jordan | Filed under: DNS, Free Geek, Insight, LDAP, Linux, Migrate, SSH, Vancouver | 2 Comments »

Free Geek Mascot #1
Today was awesome! We got so much done!!! And it all went without a problem… oh except for when we tried to create an LACP bond on our NFS server and crashed the whole network… yeah… Quick story on that. we have 10 VLANs all trunking between our switches and our router. The NFS server is on VLAN 5 untagged on port 17 on the switch, we the added port 18 and created a bond on the switch. We then created a bond0 interface on the NFS server and used ifenslave to assign the eth devices to the bond device. Then….
BAM! WHOLE NETWORK GOES DOWN. Not just vlan5, no no, the whole god damn network. No Internet access nothing, not even from the router, the router can’t ping a thing on the whole network.
Why God? Why?
Then the Network God ARP said, “Jordan did you check those top kwality DLink switches?” So off I went to check the switch I just modified. For some unknown reason the DLINK decided to plunk VLAN 6 tagged onto port 16 for no reason what-so-ever. So I fixed that, but no, nothing worked still. So Tyler says, just unplugg the ethernet cables to the NFS server. Voila! Problem solved. Basically we think the NFS was just spewing out crap across the network and making all the servers in VLAN 5 bail, including the router. We were getting some pretty crazy ARP poisoning happening the router. Now, on to the good stuff.

This is a basic (and poorly made) diagram of how the Free Geek Vancouver network looks. We’ll take a look at how an LTSP client boots and logs in.
First the LTSP client boots looking for a PXE server, DHCP is handed out and tells the client to grab a boot image from yew. The LTSP client then boots into Ubuntu 10.04 (bleeding edge baby) where the login screen is presented. The user logs in and authenticates against our new fancy LDAP server on teak. When the client logs in their home directory is handed out via LDAP as /net/home/<$user> This directory is handled by AutoFS and mounts the NFS home from maple. The user now has full desktop experience with all their account info and home directory handled by 3rd parties.

What? Centralized authentication AND home directories?! REALLY?
Our LTSP server is now a 2 x Dual Core Xeon 3.20GHz with 4GB of RAM. A HUGE upgrade from what we running before. In addition to all this insanity Vicki was able to migrate our ticketing system for us as well as update all the LDAP records for home directories, install autofs on all servers, install the mount maps, comment out all the irrelevant fstab crap AND switch over all our servers to the LDAP server. Pow vicki, pow!
The backup system is pretty sweet as well. In our NFS server that holds the home directories is two RAID 5’s, a RAID 1 and some spares. One RAID 5 has a slice out of it that is for home directories. The other is 1TB for nothing but backups. What Tyler did was write a script that uses rsync to create incremental backups all done thru hard links. It’s pretty rad.
Now that I come to think of it, I didn’t really do much except play with the dogs!!

She helped in her own way

What's going on?
Posted: May 4th, 2010 | Author: jordan | Filed under: Free Geek, LDAP, Linux, SSH | 2 Comments »
Yes, yes, I know. Two months have gone by since the last entry about Free Geek. Well finally I had some time to make it down there and to my enjoyment though Tyler from Free Geek had been busy at work. He managed to do quite a bit of work while I was away. Here’s a pic and some highlights!

Front of Rack
Now first I must mention something that happened which was spectacular. I showed up to Free Geek with tools in hand ready to kick ass and chew bubblegum. I said ‘Hi’ to the gang and then got right to work going over what’s been done already and what we should do for the day. Then I heard a small voice coming from behind me. It all started with a simple ‘Hello.’ Tyler and I turned around and here stood this lady, she said that she had heard we were doing updates to the network and wondered if she could help. I have something to confess here, I judged at first sight. So my initial response was ….. uhhhhhh….. and in my head I was thinking “oh god I have SO much to do today, I can’t possibly teach and babysit someone else.” However we said ok you can help
“what’s your name?” I asked
“Vicki” she replied.
I said “OK, Vicki, I’m going to outline on this whiteboard what we hope to accomplish today.”

Damn! That's nice wiring!
I then began drawing out network topologies and what VLAN’s we were going to roll out that day. Tyler pulls up a network diagram I had done up briefly a few weeks ago to talk about subnet allocation and service assignments. All the while Vicki was quietly watching and listening. We then went about which of our new servers would be responsible of what task, such as “teak” was going to be our new LDAP and DNS server, maple the new NFS server, how authentication was going to happen for autoFS mounts and so on. Granted if you’ve been in this industry for a while this isn’t super complex stuff, LDAP migration, network topology planning, thinking ahead for future departments, etc etc. However, this isn’t childs play either, let’s be honest there are a lot of ‘sys admins’ out there and not all of them could roll out a network of this size.
We turned to Vicki and started going thru the tasks on the board, expecting (I was anyway) to see a lot of confusion. BUT NO! OMG! She knew just as much, if not MORE about this stuff than we did. In fact, over lunch we got into a discussion about proper use of VLAN’s and subnet routing between them. This woman was (is) AMAZING! It was like the network God looked down from heaven and with his noodley appendage, blessed our tech mecca for that day by sending us a worker! A worker that new how to install services, write config files, test connectivity and map VLAN’s!!! Quite literally she cut our work time by 40% if not more. If anyone needs a good sysadmin, or network engineer who knows their way around a linux terminal and learns by being shown ONCE! Contact me, I’ll send her details on to you.
Anywho, Tyler and I laid out the VLAN’s and what they would be responsible for. We had configured three switches thus far to trunk all the VID’s but when we got to the fourth and final switch, we had no admin credentials for it. (My fault!) Our plan at that point was to wait until the end of the day, reset the switch, recover the password and then move our core router to the rack. In the meantime I checked up on Vicki and she had gotten all of our services, OpenLDAP, bind, Zenoss, apt-cache, TFTP server, and some other stuff up and running and was ready for configuration. I migrated the database from an older version of OpenLDAP with a slapd.conf file to the new version with the slapd.d directory.

Tyler and Vicki (Respectively)
Once the Free Geek came to an end Tyler and I moved the router from the bathroom server room to the upstairs rack, pushed the ADSL modem thru and VLAN, and then made an LACP trunk to our OpenBSD router. Put the VLAN interfaces in place and POW. Network configured. (For the most part) The final stage is migrating the servers to the proper VLAN’s and updating their services configurations.
The next and final post will be mostly diagram based. Stay Tuned! HOPEFULLY the next post will be really insightful IF I can get Luke and Kamil from Zymeworks to donate some time into rebuilding our Asterisk server and implementing a KDC
 Recently I was lucky enough to be a crew member on a sailboat that was making passage through the Caribbean. The Captain of the vessel, who lived aboard, was speaking to me about data storage and how difficult of an equation it was. Sailboats have very little power available to them when they’re underway as most don’t run their engine which is the only source to power the limited batteries kept onboard. He was thinking about picking up a Drobo-Mini and using SSDs to reduce the amount of draw on his system, however this solution is DAS based and doesn’t allow him access to the data unless he plugs directly into the box which means, you need a computer as well. Which is even more draw on the electrical system.
Recently I was lucky enough to be a crew member on a sailboat that was making passage through the Caribbean. The Captain of the vessel, who lived aboard, was speaking to me about data storage and how difficult of an equation it was. Sailboats have very little power available to them when they’re underway as most don’t run their engine which is the only source to power the limited batteries kept onboard. He was thinking about picking up a Drobo-Mini and using SSDs to reduce the amount of draw on his system, however this solution is DAS based and doesn’t allow him access to the data unless he plugs directly into the box which means, you need a computer as well. Which is even more draw on the electrical system. My next step to this plan would be to get the Pi to be a wireless access point as well.
My next step to this plan would be to get the Pi to be a wireless access point as well.












